-Aug-06-2023-08-58-25-5813-PM.png?width=236&name=talk2m%20(3)-Aug-06-2023-08-58-25-5813-PM.png) The need for security isn’t that apparent until part of your network or privacy is compromised. Network data security should always be a top priority when considering connectivity within a plant or to multiple sites. Security is highly important in the 21st century industrial sector as corporate espionage for sensitive inside information is becoming increasingly common.
The need for security isn’t that apparent until part of your network or privacy is compromised. Network data security should always be a top priority when considering connectivity within a plant or to multiple sites. Security is highly important in the 21st century industrial sector as corporate espionage for sensitive inside information is becoming increasingly common.
One of the key challenges the industrial sector is facing in this regard is managing their apparatus with the right person. The requirements are getting more blurred, and it is becoming difficult to decide whether an engineer, PLC technician or an IT expert is required to ensure smooth sailing. Finding the right solution has therefore been a source of frustration for too long, leading to inefficiencies.
Taking these difficulties under consideration, eWON has created a top-notch Remote Access Solution that provides layered, fool-proof security for your industrial networks, while injecting ease of use for end users & IT managers alike.
Security, integrity & reliability are the three core cornerstones of eWON’s Talk2M cloud infrastructure. eWON has followed an in-depth approach based on the guidelines set forth by ISO27002, IEC 62443-2-4 and NIST Cyber Security Framework 1.0 to ensure security is fully integrated at every level within the solution.
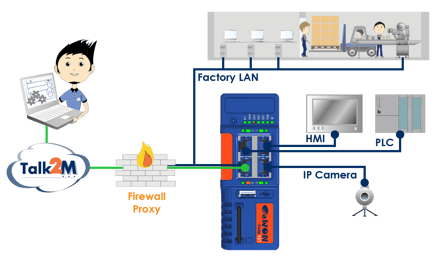
The Talk2M infrastructure is a highly integrated & synchronous part of the remote access solution provided by eWON. Spread over a network of distributed access servers, VPN servers and other services, it acts as a central convergence point for eWON and its users. Talk2M services are always hosted within best-in-class, SOC1, SOC2 and ISO 270001:2005 certified data centers. The network of servers is monitored at all times so that the end-users enjoy maximum availability, within a secure environment that’s powered by Intrusion Detection Systems, Host Intrusion Prevention Systems and an array of alerting mechanisms.
eWon’s Hardware Devices

The eWon Talk2M unit is generally installed in the machine’s control panel, sitting in between the machine’s network and the factory’s network. Whenever a connection needs to be established between the two, eWON acts as a gateway for the traffic. As soon as eWON is configured for VPN access, filtration of traffic kicks off, and only those devices that are part of the policy-set are provided access.
In addition, eWON devices provide user-level access segregation, allowing only appropriate users to have access & configuration rights. As all eWON devices feature a digital input, a switch can be connected to the input and be used to enable/disable the WAN port. This means that the end user has complete control of the network at all times.
Within eWON’s eCatcher application, Talk2M account administrators can configure filtering & firewalling rules as to which devices are accessible remotely. The application provides complete & transparent controls over the configuration, allowing the user to change the ports, protocols and other network parameters.
This means that at the end of the day, you’ll have a network that fits your organization’s requirement, and not one that’s based on a template. However, if necessary, one can choose from the 4 different firewall setting rules provided by Talk2M, i.e. Standard, High, Enforced & Ultra.
The SSL/TLS protocol is employed to provide cutting edge encryption to communications between the remote user and the eWON device. Data authenticity, confidentiality and integrity are ensured at all times so that espionage or penetration remain out of the equation.
User & Access Management
Talk2M provides comprehensive & thorough user & access management to administrators, thus allowing rule-based access to network infrastructure. eCatcher servers as a secure authentication platform to ensure that device access security is never compromised from the outside. Password enforcement and two-factor authentication are also available, if required.
On the Talk2M connection report, every remote connection is documented, serving as an extremely powerful auditing tool. This provides account administrators with enough power to stop an attack in its midst, or trace back to the source of a penetration.
Policy Compliance
As stated earlier, eWON doesn’t force templates upon you, instead it molds itself according to your needs. The eWON/Talk2M solution is highly flexible, and compatible with the existing corporate security policies & rules that your business has. Talk2M makes use of outbound connections over commonly open ports, i.e. 443 & 1194, and therefore is compatible with most proxy servers & firewalls, while being minimally intrusive on the network.
You may also be interested in reading:



-Aug-06-2023-09-00-29-1471-PM.png?width=600&height=200&name=ewon%20catalogs%20(1)-Aug-06-2023-09-00-29-1471-PM.png)